Introduction
Computer offences in New South Wales (NSW) are treated with the utmost seriousness, reflecting the significant impact cybercrime can have on individuals and organisations alike. Understanding the complexities of these laws is essential for effectively safeguarding personal and sensitive information in an increasingly digital world.
Recognising the importance of navigating cybercrime laws helps individuals and businesses protect themselves against unauthorised access, data impairment, and other malicious activities. This guide aims to provide a comprehensive overview of computer offences in NSW, highlighting the critical need for awareness and compliance.
Types of Computer Offences
Unauthorised Access of Restricted Data
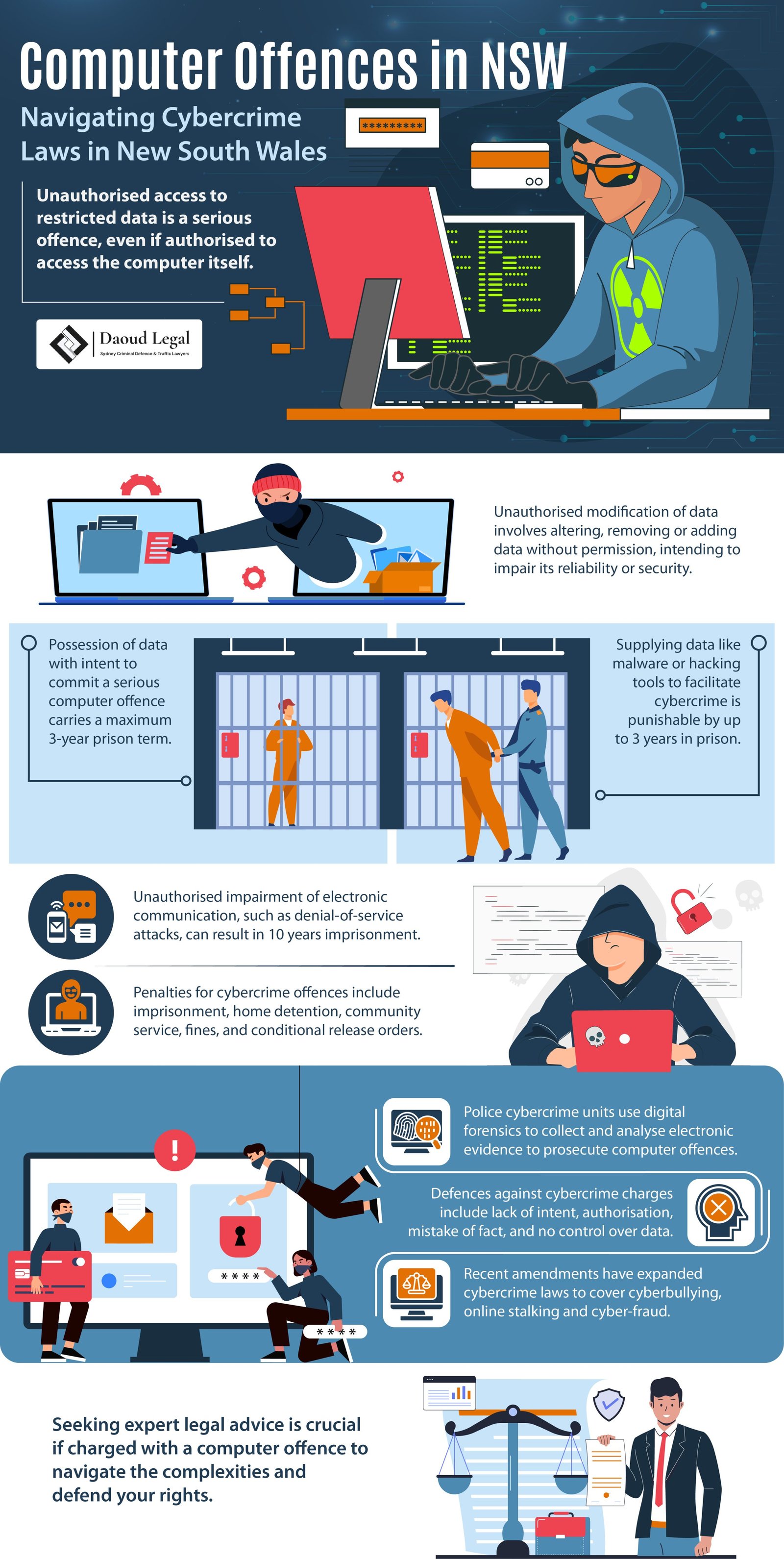
Unauthorised access to restricted data held in a computer is a significant offence under section 308H of the Crimes Act 1900 (NSW). This offence occurs when a person accesses or modifies restricted data without proper authorisation, knowing that their access or modification is unauthorised, and intending to cause that access or modification. Actions that may constitute unauthorised access include:
- Accessing files without the necessary permissions, even if authorised to access the computer itself.
- Copying or moving data to external storage devices like USB sticks or hard drives.
- Allowing unauthorised individuals to access specific programs or files through one’s actions.
To secure a conviction, the police must prove beyond a reasonable doubt that the individual caused unauthorised access or modification, knew it was unauthorised, and intended to cause that access or modification.
Unauthorised Modification of Data
The offence of unauthorised modification of data with intent to cause impairment is outlined in section 308D of the Crimes Act 1900 (NSW). This offence involves altering, removing, or adding data in a computer without authorisation, intending to impair access to, or the reliability, security, or operation of the data. The maximum penalty for this offence is ten years imprisonment.
Actions that may constitute unauthorised modification include:
- Deleting or altering information stored on a computer without permission.
- Adding erroneous data to disrupt the reliability or security of existing information.
- Introducing malicious software to impair computer operations.
Additionally, section 308I addresses unauthorised impairment of data held in devices such as computer disks or credit cards, carrying a maximum penalty of two years imprisonment. Both sections require that the individual knows the modification is unauthorised and intends to cause impairment.
To convict someone of unauthorised modification, the police must demonstrate that the individual caused the modification, knew it was unauthorised, and intended to cause impairment.
Possession with Intent to Commit a Serious Computer Offence
Possession of data with intent to commit a serious computer offence is addressed under section 308F of the Crimes Act 1900 (NSW). This offence occurs when a person possesses or controls data intending to commit or facilitating the commission of a serious computer offence, whether by themselves or another person. The maximum penalty for this offence is three years imprisonment.
Actions that may constitute possession with intent include:
- Owning a computer or data storage device containing illicit data.
- Controlling data stored on another person’s computer, within or outside the jurisdiction.
- Holding documents that record unauthorised data with the intent to use them for committing cybercrime.
To obtain a conviction, the police must prove that the individual was in possession or control of the data, intended to commit or facilitate a serious computer offence, and that the intended offence was severe as defined by sections 308C, 308D, or 308E.
Supplying Data with Intent
Supplying data with intent to commit a serious computer offence is governed by section 308G of the Crimes Act 1900 (NSW). This offence involves producing, supplying, or obtaining data intending to commit or facilitating a serious computer offence. The maximum penalty for this offence is three years imprisonment.
Examples of actions that may constitute supplying data with intent include:
- Distributing malware or viruses designed to impair computer systems.
- Providing hacking tools or software to others with the intent that they use them for cybercrime.
- Sharing confidential or restricted data to facilitate identity theft or online fraud.
To secure a conviction, the police must demonstrate that the individual produced, supplied, or obtained the data, intended to commit or facilitate a serious computer offence, and that the intended offence was severe as outlined in sections 308C, 308D, 308E, or committed in another jurisdiction but would be liable under NSW law.
Unauthorised Impairment of Electronic Communication
Unauthorised impairment of electronic communication is defined under section 308E of the Crimes Act 1900 (NSW). This offence involves disrupting or interfering with electronic communications to or from a computer without proper authorisation, knowing that such impairment is unauthorised, and intending to cause the disruption.
Examples of actions that may constitute unauthorised impairment include:
- Launching denial of service (DoS) attacks to disrupt online services.
- Interfering with email communications to prevent messages from being sent or received.
- Tampering with network connections to impair internet access.
To convict someone of unauthorised impairment, the police must prove that the individual caused the impairment, knew it was unauthorised, and intended to disrupt the electronic communication.
Get Immediate Legal Help Now.
Available 24/7
Types of Penalties for Cybercrime Offences
Courts in NSW have a range of penalties they can impose for cybercrime offences. The specific penalty depends on several factors, including the nature and severity of the offence, the offender’s intent, and the harm caused. Below is an overview of the penalties that may be imposed.
- Imprisonment: Imprisonment is the most severe penalty, involving full-time detention in a correctional facility. The maximum term of imprisonment varies depending on the specific offence.
- Alternative Sentencing Options: For less severe offences or where imprisonment is not deemed necessary, courts may impose alternative sentences, including:
- Home Detention – This allows the offender to serve their sentence at their home under strict supervision and electronic monitoring. Home detention is no longer a stand-alone order but can be imposed as a condition of an Intensive Corrections Order (ICO).
- Intensive Corrections Order (ICO) – This replaces periodic detention and includes conditions such as attending counselling or treatment, complying with a curfew, abstaining from alcohol, and performing community service.
- Community Corrections Order (CCO) – This order requires the offender to adhere to standard conditions, such as not committing further offences and appearing before the court when required. Additional conditions may also be imposed by the court or a community corrections officer. CCOs replaced Community Service Orders (CSO) and Good Behaviour Bonds.
- Financial and Non-Custodial Penalties: Courts may also impose financial penalties or other noncustodial sentences, including:
- Fines – The amount is determined based on the offender’s financial situation and ability to pay.
- Conditional Release Order (CRO) – This includes standard conditions such as refraining from further offences and appearing before the court when required.
- Section 10A – A conviction is recorded, but no further penalty is imposed.
- Section 10 Dismissal – Under a Section 10 dismissal, the court dismisses the charges without a conviction, meaning no penalty or criminal record is imposed.
Maximum Penalties for Cybercrime Offences
| Section | Offence | Maximum Penalty |
|---|---|---|
| Penalties for Unauthorised Access and Modification | ||
| Section 308C | Unauthorised Access with Intent | Equivalent to the serious indictable offence intended to be committed |
| Section 308D | Unauthorised Modification of Data with Intent to Cause Impairment | Imprisonment for up to 10 years |
| Section 308H | Unauthorised Access to or Modification of Restricted Data | Imprisonment for up to 2 years |
| Section 308I | Unauthorised Impairment of Data Held in Computer Disk, Credit Card, or Other Device | Imprisonment for up to 2 years |
| Penalties for Possession and Supplying Data | ||
| Section 308F | Possession of Data with Intent to Commit Serious Computer Offence | Imprisonment for up to 3 years |
| Section 308G | Supplying Data with Intent to Commit Serious Computer Offence | Imprisonment for up to 3 years |
| Penalties for Unauthorised Impairment and Communication Interference | ||
| Section 308E | Unauthorised Impairment of Electronic Communication | Imprisonment for up to 10 years |
| Section 308I | Unauthorised Impairment of Data | Imprisonment for up to 2 years |
Legal Defences Against Computer Offence Charges
Lack of Intent
To establish a defence based on lack of intent, the defendant must demonstrate that they did not intend to commit or facilitate the intended computer offence. This can be achieved by showing that there was no intention to commit the offence, even if an attempt was made.
- Absence of Intention: If the defendant did not intend to commit the serious computer offence, they may not be guilty of the charge.
- Attempt to Commit: Under sections 308F and 308G, attempting to commit an offence does not constitute the offence, allowing for a defence if there was an attempt but no completion.
Authorisation and Legitimate Access
A common defence is proving that the accused had authorised or legitimate access to the data or systems involved in the offence. This entails demonstrating that the access was permitted under specific circumstances or roles.
- Authorised Personnel: If the defendant was authorised to access or modify the data as part of their employment or role, this may serve as a valid defence.
- Legitimate Reasons: Accessing restricted data under legitimate reasons, such as for maintenance or security checks, can negate the unauthorised nature of the offence.
Mistake of Fact
Mistake of fact occurs when the defendant had an honest and reasonable belief in a set of facts that, if true, negate the criminal intent. This can serve as a defence if the mistake renders the accused innocent of the offence.
- Honest Belief: The defendant genuinely believed they had permission or were authorised when accessing or modifying data.
- Reasonableness: The belief must be one that a reasonable person in the same circumstances would hold.
Defence Against Possession and Supply of Data
Specific defences are available for offences related to the possession and supply of data with intent to commit a computer offence.
- Lack of Intent: Demonstrating that there was no intent to use the data to commit a computer offence can negate the offence, as intent is a requisite element.
- No Control: If the defendant did not have control over the data possessed, they may not be liable under the possession offence.
Speak to a Lawyer Today.
Available 24/7
Investigation and Prosecution Process
Role of the Police and Digital Forensics
In NSW, the Police Force plays a central role in investigating computer offences. Specialised cybercrime units within the police utilise digital forensics to collect, preserve, and analyse electronic evidence essential for prosecuting these offences. Digital forensics involves examining computer systems, networks, and digital storage devices to uncover unauthorised access, data breaches, and other cybercrime. By employing advanced forensic tools and methodologies, police can trace cybercriminal activities, recover deleted or hidden data, and establish a timeline of events critical to building a strong prosecution case. Collaboration with other law enforcement agencies and adherence to legal protocols ensure that the evidence gathered is admissible in court.
Court Proceedings and Case Management
Once an investigation is completed, cases involving computer offences proceed through the court system based on the severity and nature of the offence. Offences categorised as Table 1 offences, such as possession of data with intent to commit a serious computer offence (section 308F) or supplying data with intent (section 308G), are typically heard in the Local Court. However, either the prosecutor or defendant may elect to have the matter heard in the District Court, where higher penalties can be imposed.
During court proceedings, evidence collected through digital forensics is presented to demonstrate the defendant’s involvement in the offence. The court follows a structured case management process to ensure that cases are handled efficiently and that all legal procedures are properly observed. Factors such as the intent, the extent of data impairment, and the harm caused by the offence are considered when determining the appropriate penalties. This structured approach ensures that justice is served while upholding the integrity of the legal system in addressing cybercrime. It is crucial to seek the right legal advice from an early stage to ensure you remain compliant with the court procedures and processes.
Recent Amendments and Trends in Cybercrime Laws
Updates to the Crimes Act
Recent legislative changes in NSW have significantly expanded the scope of cybercrime offences under the Crimes Act 1900 (NSW). Notably, an amendment bill passed on 21 November 2024 has redefined certain offences to include cyber-related activities. This amendment specifically addresses cyberbullying by incorporating it into the definition of intimidation under section 7 of the Crimes (Domestic and Personal Violence) Act 2007 (NSW).
Key updates include:
- Inclusion of Cyberbullying as Intimidation: The amendment ensures that online harassment and threatening messages are projectable under existing intimidation laws.
- Expanded Stalking Definitions: Section 8 of the Act now covers stalking conducted via the internet or other technologically assisted means, broadening the legal framework to address modern cyber harassment methods.
- Enhanced Penalties: Offences such as stalking or intimidation with the intent to cause fear of physical or mental harm are now punishable by up to five years imprisonment and/or a fine of $5,500.
These changes reflect the NSW government’s commitment to adapting legal measures in response to evolving cyber threats and ensuring comprehensive protection against digital harassment.
Emerging Trends in Cyber Offences
The landscape of cybercrime in NSW continues to evolve, with several emerging trends shaping the way laws are enforced and prosecuted. Recent statistics indicate a significant rise in cyber-related offences, prompting the establishment of specialised units and the adoption of advanced investigative techniques.
Notable trends include:
- Increase in Cyber-Fraud and Online Scams: There has been a substantial growth in activities such as phishing, identity theft, and online fraud, exploiting vulnerabilities in digital platforms to deceive and steal from individuals and organisations.
- Example: The rise in phishing attacks targeting financial information has led to stricter monitoring and quicker response strategies by law enforcement agencies.
- Growth of Cyber-Extortion and Ransomware Attacks: Cybercriminals are increasingly using ransomware to lock down critical data, demanding payment for its release. This trend poses significant challenges for both public and private sectors in safeguarding sensitive information.
- Example: High-profile ransomware attacks on healthcare institutions have highlighted the need for robust cybersecurity measures and rapid incident response protocols.
- Expansion of Cybercrime Units: In response to the growing threat, NSW Police has established dedicated cybercrime squads focused on combating online offences. These units are equipped with specialised training and technological tools to effectively investigate and prosecute cybercriminals.
- Example: The first stand-alone cybercrime squad was launched in 2024, resulting in a noticeable increase in cybercrime-related arrests and convictions.
- Legislative Adaptations to Technological Advances: As technology evolves, so do the methods employed by cybercriminals. NSW law continuously adapts to address new forms of cybercrime, ensuring that legal provisions remain effective against sophisticated cyber threats.
- Example: Amendments to the Crimes Act 1900 (NSW) have been made to cover crimes facilitated by advanced technologies such as artificial intelligence and blockchain.
These emerging trends underscore the dynamic nature of cybercrime and the necessity for ongoing legislative and technological advancements to effectively counteract these threats.
Conclusion
Computer offences in NSW are treated with exceptional seriousness, encompassing a wide range of activities such as unauthorised access, data modification, cyber fraud, and impairment of electronic communication, each governed under the Crimes Act 1900 (NSW). These offences carry stringent penalties, underscoring the importance of understanding the legal framework to effectively safeguard personal and organisational data against cyber threats.
If you have been charged with a computer offence, it is imperative to seek expert legal advice promptly. Our team of specialised lawyers offers proven solutions and unparalleled expertise to help navigate the complexities of cybercrime laws in NSW and defend your rights effectively. Schedule a consultation now!




